What is Shadow IT?
Shadow IT describes the procurement and use of IT-related hardware, software, or services such as telecom connectivity, without the explicit approval of the IT department in an organization. This practice is most often driven by well-intentioned, but busy business leaders of varying departments within an organization wanting to increase the productivity of their teams, eliminate bottlenecks, and provide immediate problem solving to most quickly serve their customers or business stakeholders. Digital transformative technologies are adopted and implemented by business unit leaders and their departments to address these needs, causing decentralization of the technology environment within an organization. This creates a gap between business units and the IT department known as Shadow IT.
Shadow IT creates the danger of the unknown. And if each department is adding technologies or services without IT’s knowledge – decentralizing the technology environment within the organization – this both exposes your company data and eats up your IT budget. Decentralization causes a greater lack of visibility into what assets are owned, what applications are being accessed, what connectivity services are in or out of contract, and as result, over-payment of resources. The need for digital transformation is contributing to a decentralized technology environment for many organizations, driving more Shadow IT as a result.
Cybersecurity Risks Are Lurking In The Shadows
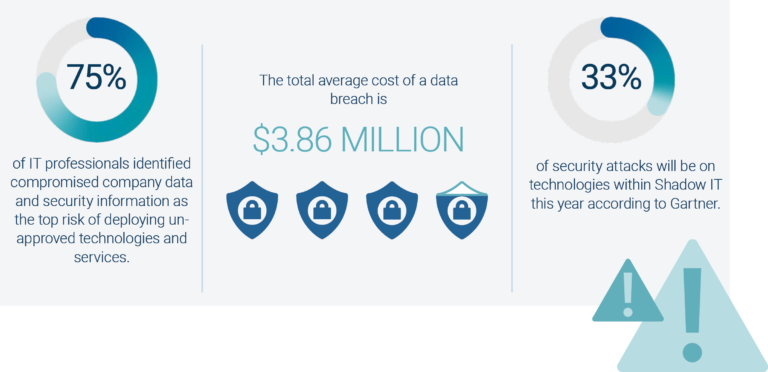
Shadow IT introduces security gaps to an organization. Because the decentralized technologies associated with Shadow IT haven’t been vetted by the IT department, it doesn’t undergo the same security procedures as other supported technologies. In fact, 75% of IT professionals identified compromised company data and security information as the top risk of deploying unapproved technologies and services. Further, according to Gartner, 33% of security attacks will be on technologies within Shadow IT this year, and with the total average cost of a data breach clocking in at $3.86 million, any risk to an organization must be addressed immediately. To complicate matters, even more, Shadow IT increases the likelihood of uncontrolled data flows leading to serious compliance issues as it prevents an organization from having proper documentation and approval of technologies to meet compliance and regulations.
Below are some of the biggest cybersecurity risks Shadow IT creates:
- Holes in Security – Shadow IT, when left unchecked, creates dangerous holes in an organization’s security environment. This opens the door to cybercriminals and makes it easier for threat actors to gain access to critical information. The massive shift towards adopting digital transformative tech, such as SaaS tools, makes it harder to know where these holes exist, causing security departments to implement cloud-based monitoring tools.
- Low Visibility – Organizations need full visibility into their technology environment to be able to accurately detect all threats before they evolve and cause a data breach. Shadow IT makes this impossible because all unsanctioned devices, software, and services aren’t seen by the IT department…they can’t fix what they can’t see.
- Increased Possibility Of Data Loss – Employees who store data in personal cloud file-hosting services and on personal devices significantly increase the possibility of data loss. Most employees do not worry about implementing backup technologies, so this information is left unprotected.
- Compliance Issues – Shadow IT creates uncontrolled data flow that can lead to serious compliance issues for the organizations. The Discovery of unapproved software can force government entities to audit a company’s infrastructure, leading to hefty fines.
- Disrupted Workflows – When employees are choosing their own tools and platforms, the potential for non-compatible file types increases. It also becomes difficult for employees to collaborate across the organization when they have several different tools that all do essentially the same thing.
Shining the Light on Shadow IT
To help combat these security and compliance risks, it takes gaining and maintaining visibility into Shadow IT and the whole picture of the technology environment. Service partners can help, but it’s also a good idea to educate your employees and end-users on technologies that are already available through the organization that has been vetted by IT. Many times, employees are unaware of the technologies available to them and that is why they take matters into their own hands and implement new technology without IT involvement. Additionally, employee security awareness educates users on the security risks associated with implementing technologies without going through IT first. It’s a good idea to have a policy and process in place for employees to go through IT to get new technologies for their departments.
At One Source, we merge technology, industry knowledge, and dedicated team members to provide our clients with a centralized approach to their technology environment using asset inventory, invoice management/auditing, contract management, and cost recovery. Our processes and technology enable us to have real-time visibility into our clients’ technology and connectivity costs allowing their teams to focus on other high-impact tasks.
Ready to start your next project?
Send a request to speak with a One Source technology advisor.



